Recently, a malvertising campaign was spotted that tricked users by simulating a Windows update in the browser to deliver Aurora malware.
Written in Golang, Aurora has been available on various hacker forums for more than a year, advertised as an info stealer with extensive capabilities and low antivirus detection.
According to researchers at Malwarebytes, the malvertising operation relies on popunder ads on adult content websites with high-traffic adult content and redirects potential victims to a malware-serving location.
It’s not a Windows update
Popunder ads are cheap ‘pop-up’ ads that launch behind the active browser window, staying hidden from the user until they close or move the main browser window.
In December last year, Google reported that popunders were used in an ad fraud campaign that amassed hundreds of thousands of visitors and tens of millions of fraudulent ad impressions.
The more recent one spotted by Malwarebytes has a much lower impact, with close to 30,000 users redirected and almost 600 downloaded and installed the data-stealing malware on their systems.
A threat actor created a clever idea in which the popunder simulates the Windows system update screen by rendering a fullscreen browser window.
Researchers tracked over a dozen domains that were used in these campaigns. Many of them appeared to be adult websites and simulated a fake Windows update.
- Activessd[.]ru
- chistauyavoda[.]ru
- xxxxxxxxxxxxxxx[.]ru
- Activehdd[.]ru
- oled8kultra[.]ru
- xhamster-18[.]ru
- oled8kultra[.]Sites that you can use to learn more about
- activessd6[.]ru
- activedebian[.]ru
- shluhapizdec[.]ru
- 04042023[.]ru
- Clickasdfer[.]ru
- moskovpizda[.]ru
- pochelvpizdy[.]ru
- Evatds[.]ru
- click7adilla[.]ru
- grhfgetraeg6yrt[.]Sites that you can use to learn more about
All of them served for download a file named “ChromeUpdate.exe,” revealing the deception of the full-screen browser screen; however, some users were still tricked into deploying the malicious executable.
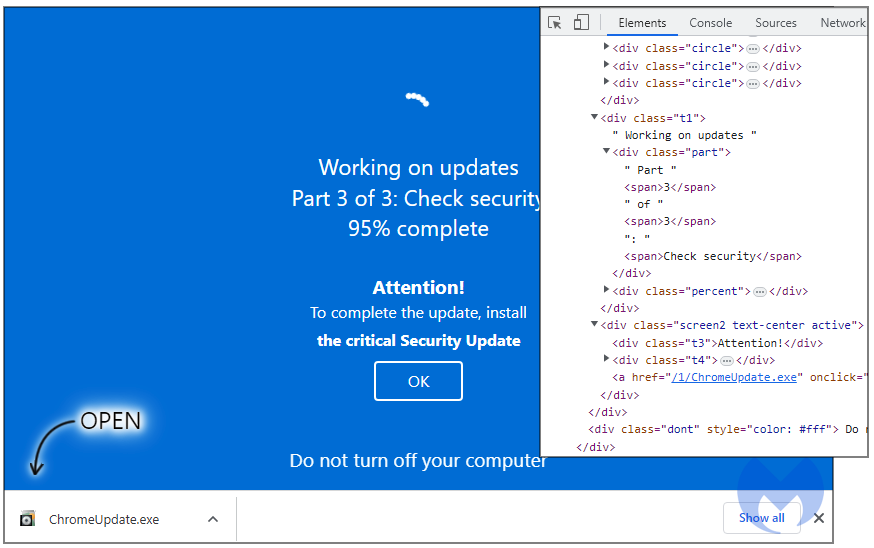
New malware loader
The alleged Chrome updater is a so called “fully undetectable” (FUD) malware loader called ‘Invalid Printer’ that seems to be used exclusively by this particular threat actor.
Malwarebytes says that when its analysts discovered ‘Invalid Printer,’ no antivirus engines on Virus Total flagged it as malicious. The detection rate increased a few months later after Morphisec published a report on the issue.
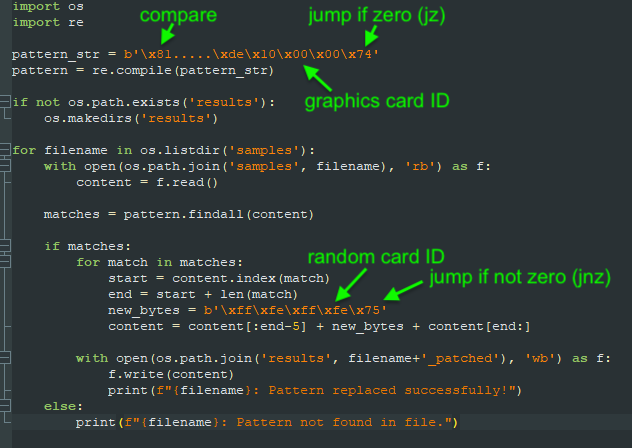
Invalid Printer first checks the host’s graphic card to determine if it’s running on a virtual machine or in a sandbox environment. Researchers found that if it isn’t, Invalid Printer unpacks a copy and launches it.
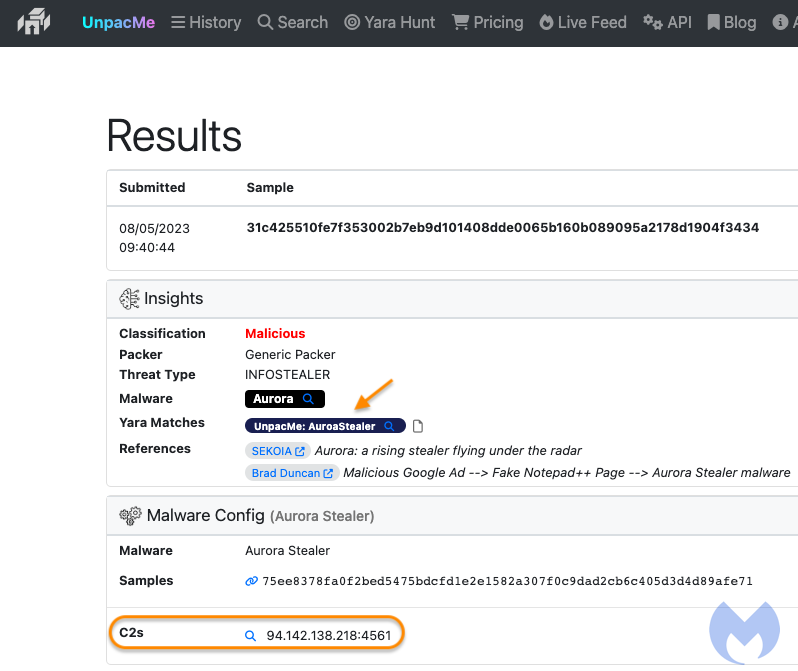
Malwarebytes says that the threat actors behind this campaign are particularly interested in creating difficult-to-detect software. They upload new samples onto Virus Total every day to test how well they do against detection engines.
Jérôme Segura, director of threat intelligence at Malwarebytes, noticed that every time a new sample was first submitted to Virus Total it came from a user in Turkey and that “in many instances the file name looked like it had come fresh from the compiler (i.e. build1_enc_s.exe).”
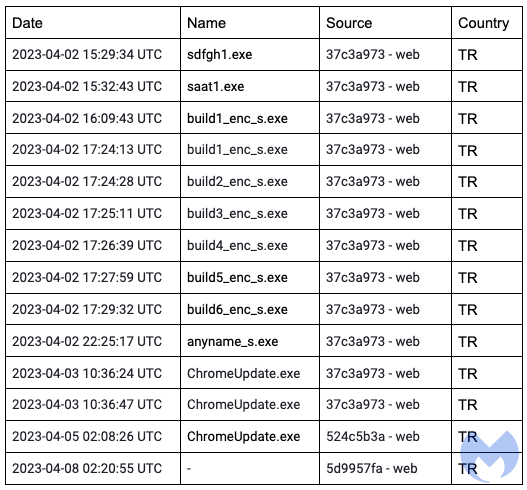
Further investigation revealed the threat actor uses an Amadey Panel, which could indicate the use of well-documented malware and reconnaissance tools. He also targets Ukrainians with tech support scams.
Malwarebytes is a software that provides technical analysis on the installation of malware and its behavior. It also includes a list of indicators for compromise, which companies and security vendors may use to protect their customers.


